Enterprise single sign-on using Security Assertion Markup Language (SAML) protocol.
- User attempts to access your application
- System redirects to the Identity Provider (IdP)
- User authenticates with the IdP and IdP generates a SAML assertion (token).
- User is redirected back to your application with the SAML assertion. System validates the SAML assertion. Upon successful validation, access is granted
Configuration To enable SAML SSO:
- Register your application with your Identity Provider: - Upload certificate - Configure SAML attributes and mappings - Note the IdP metadata URL or download metadata XML
- In your application: - Navigate to Authentication Settings - Click on settings button in “SAML SSO”.
- You can either upload the IdP metadata or enter manually the entryPoint SSO Url and Email attribute Key 4.. Click on Save button
To enable SAML authentication, you need to configure your Identity Provider (IdP) and specify the attribute name that contains the user’s email address in the SAML response.
Different IdPs may use different names for this field.
Set Up the Recipient URLs and Audience in the IdP Settings
Enter the Required URLs Recipient URL: This is where the SAML response will be sent after authentication which is (your-frontend-url/api/v1/saml/signin/callback) Example: https://f7f0-240.ngrok-free.app/api/v1/saml/signin/callback- Audience (Audience Restriction): This is used to verify the intended recipient of the SAML response.
Keep it as pageipesHub
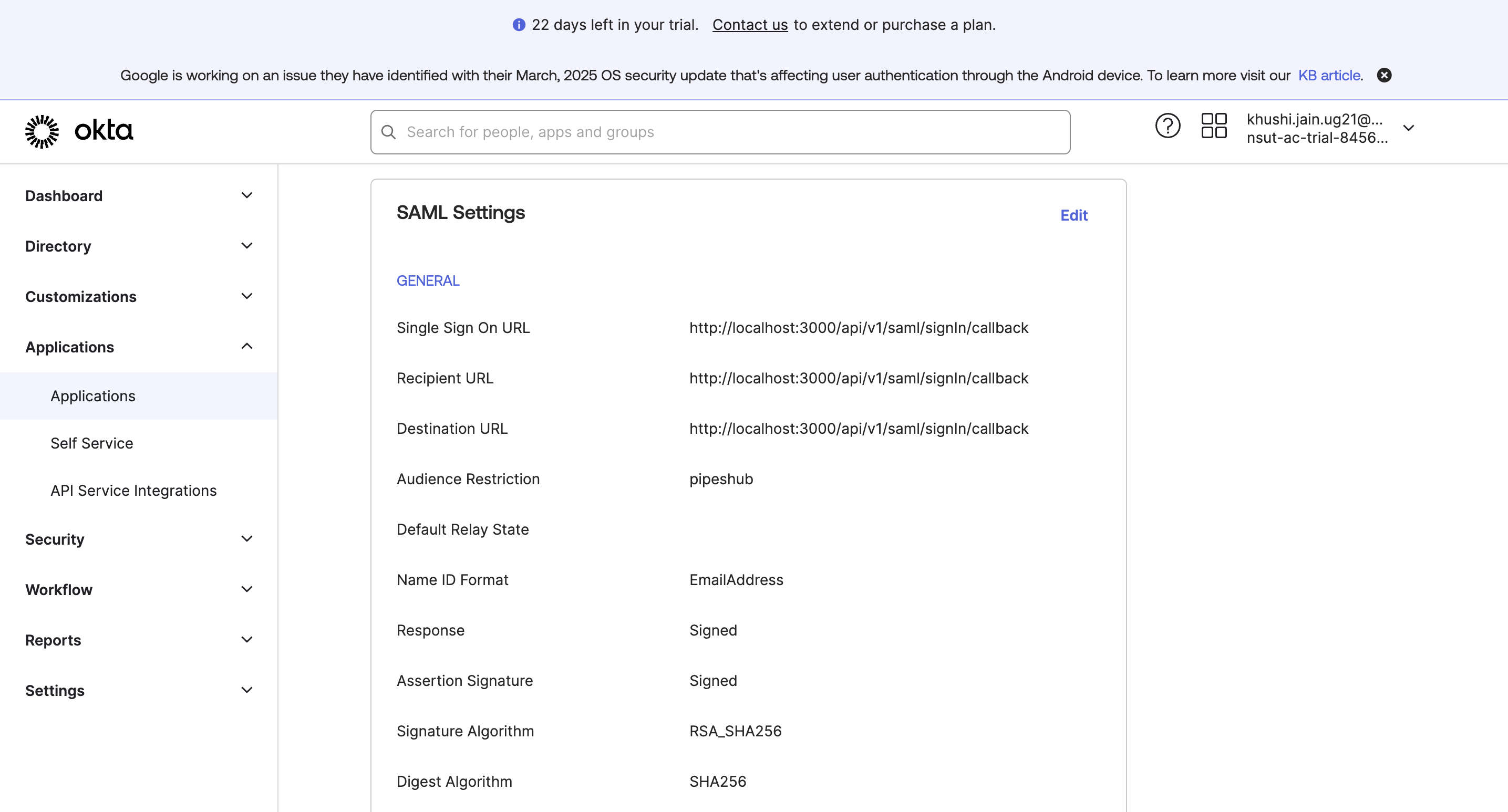
Here is the example for setting in Okta
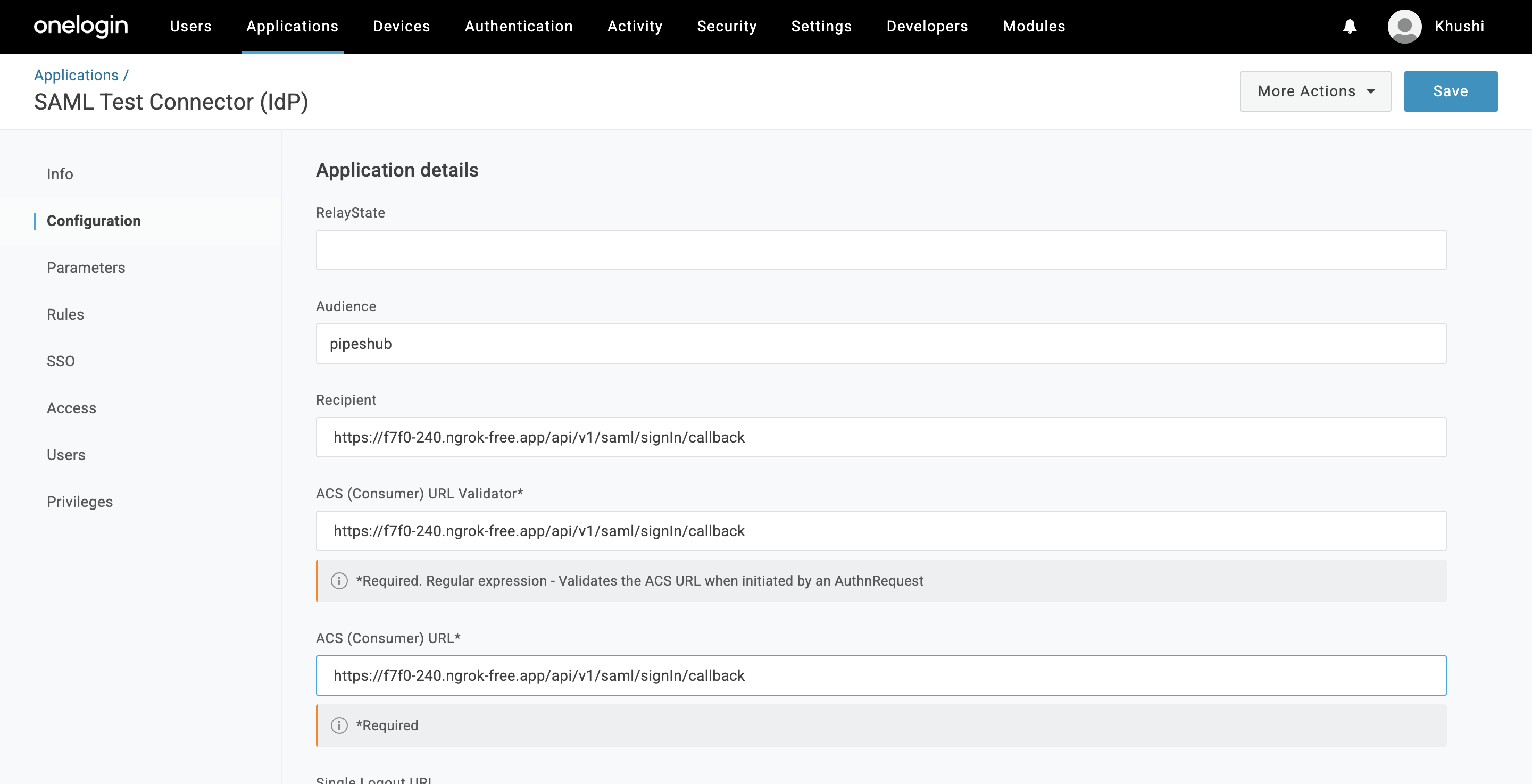
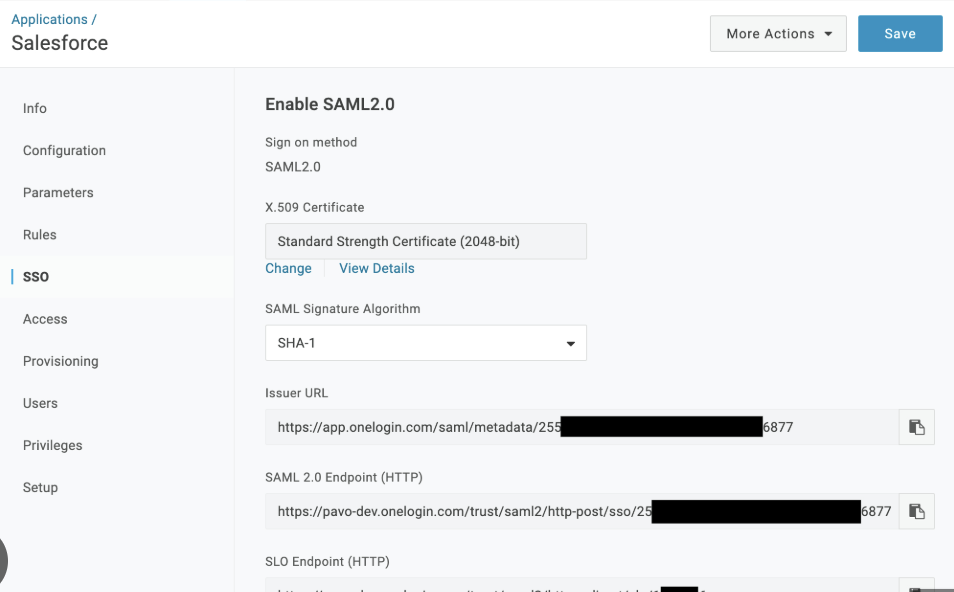
Here is the example for setting in OneLogin
What is Email Attribute Key
When a user logs in using SAML, the IdP sends a SAML response containing user details. The email address may be sent under different attribute names, depending on the IdP. You must enter the correct attribute name in our system so we can extract the email and verify the user.Where to find the Email Attribute Key
Method 1 : Through Settings of Identity Provider- Check Your IdP’s SAML Attribute Mapping
- Log in to your IdP Admin Console (e.g., Okta, Azure, Google, etc.).
- Navigate to SAML Attribute Mapping or Claims settings. Look for the attribute that contains the user email address.
- If you’re unsure, you can manually inspect the SAML response:
- Use SAML Tracer (a browser extension for Chrome/Firefox).
- Perform a login and capture the SAML response.
- Look for the email field in the response.
| Identity Provider | Common Email Attribute Name |
|---|---|
| Okta | NameID |
| Google Workspace | email |
| OneLogin | NameID / User.Email |
| Custom IdP | (Check your IdP settings) |