Microsoft SharePoint
Document management and collaboration platform
✅ Ready📝 Documentation Available
Overview
SharePoint is a web-based collaborative platform developed by Microsoft. It’s primarily used for document management and storage, acting as a secure place where teams can store, organize, share, and access information from almost any device.Key Functions of SharePoint
- Intranets & Team Sites: Serves as a centralized intranet and a secure digital space for team collaboration and internal communication.
- Document Management: Offers secure storage, version control, and organization for all documents and files.
- Content & Data Tracking: Allows users to create custom lists (e.g., tasks, contacts, issues) and manage company data.
- Workflow Automation: Enables the building of simple custom applications and forms to automate business processes.
Configuration Setup
Setup Guide
Setup Guide
Step 1: Register Application in Azure Portal
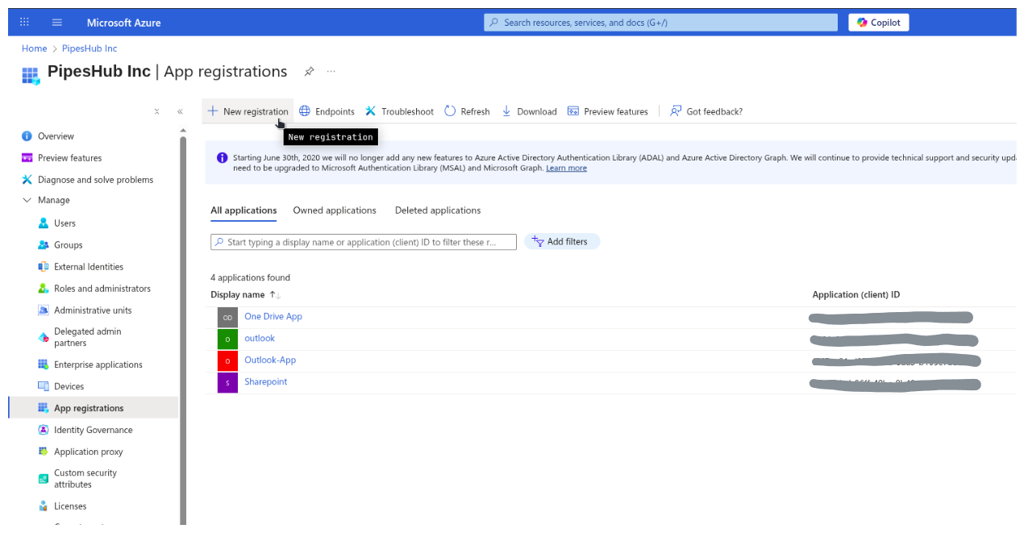
Sign in to Azure Portal:- Navigate to portal.azure.com and sign in with your Microsoft 365 administrator account
- Search for “App registrations” in the top search bar
- Or navigate to Microsoft Entra ID → App registrations
- Enter application details:
- Name: Enter app name (e.g., “PipesHub Connector”)
- Supported account types: Select “Accounts in this organizational directory only (Single tenant)”
- Select a platform: Web
- Redirect URI: Leave blank
- Click “Register”
Single-tenant configuration ensures the application only works within your organization for better security.
Step 2: Copy Application Credentials
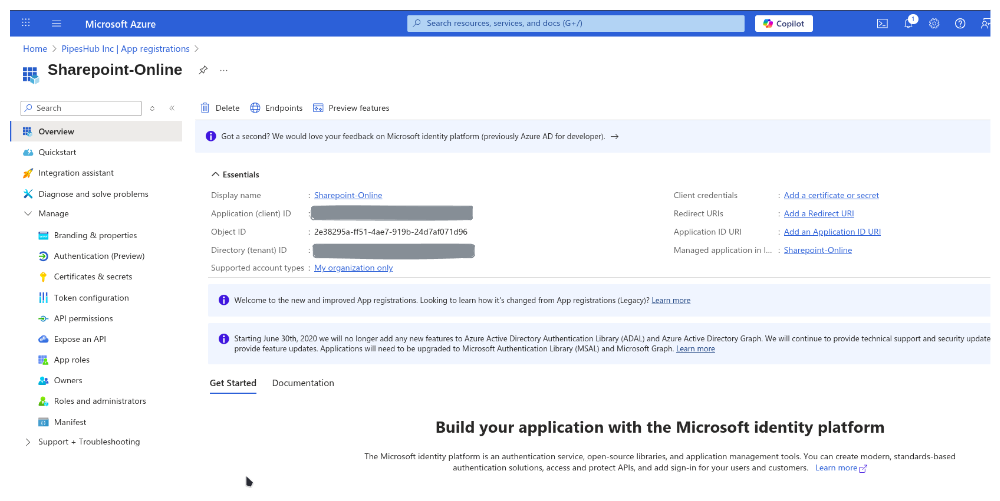
After registration, you’ll see the Overview page. Copy the following values (you’ll need these later):- Application (client) ID: Found under “Essentials” section
- Directory (tenant) ID: Found under “Essentials” section
Step 3: Configure API Permissions
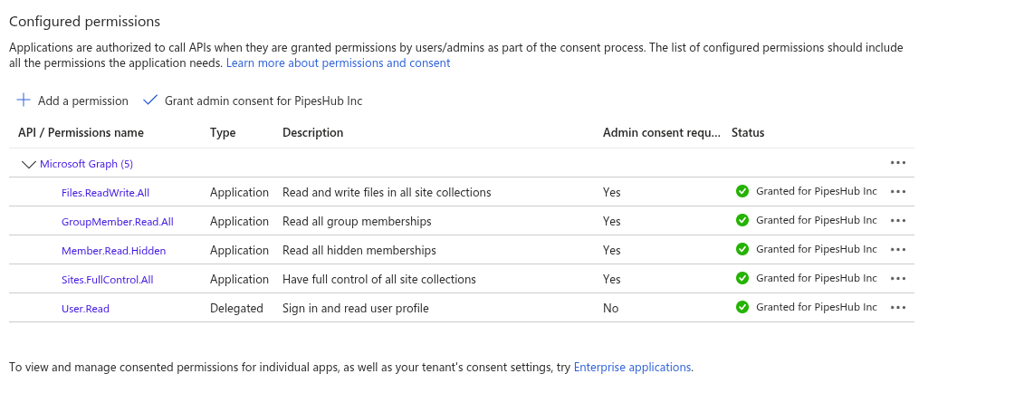
Configure Microsoft Graph Permissions:- On the overview page, click on Manage > API Permissions
- Click Add a permission
- Select Microsoft Graph
- Choose Application permissions (not Delegated permissions) and add the following:
User.Read.AllGroupMember.Read.AllGroup.Read.AllFiles.ReadWrite.AllReports.Read.AllSites.FullControl.AllMember.Read.Hidden
- Click Add a permission and select SharePoint
- Choose Application permissions and add the following:
Sites.FullControl.All
- Click Add permissions
Step 4: Grant Admin Consent
- On the API permissions page, click “Grant admin consent for [Your Organization]”
- Confirm by clicking “Yes”
- Wait for the status to show green checkmarks
Admin consent is required for application permissions. Only Global Administrators or Application Administrators can grant this consent.
Step 5: Setup Certificate & Secret
Install OpenSSL:OpenSSL is installed by default on Linux and OS X terminals. If you are using Windows, follow these instructions:- Download the relevant OpenSSL installation manager for your version of Windows. OpenSSL offers a list of third-party binary distributions, with Shining Light Productions as an option.
- During the installation process, select the option to copy the OpenSSL binaries into the
/bindirectory. - Open a new PowerShell instance. In PowerShell, you can run the following command to make use of OpenSSL binaries:
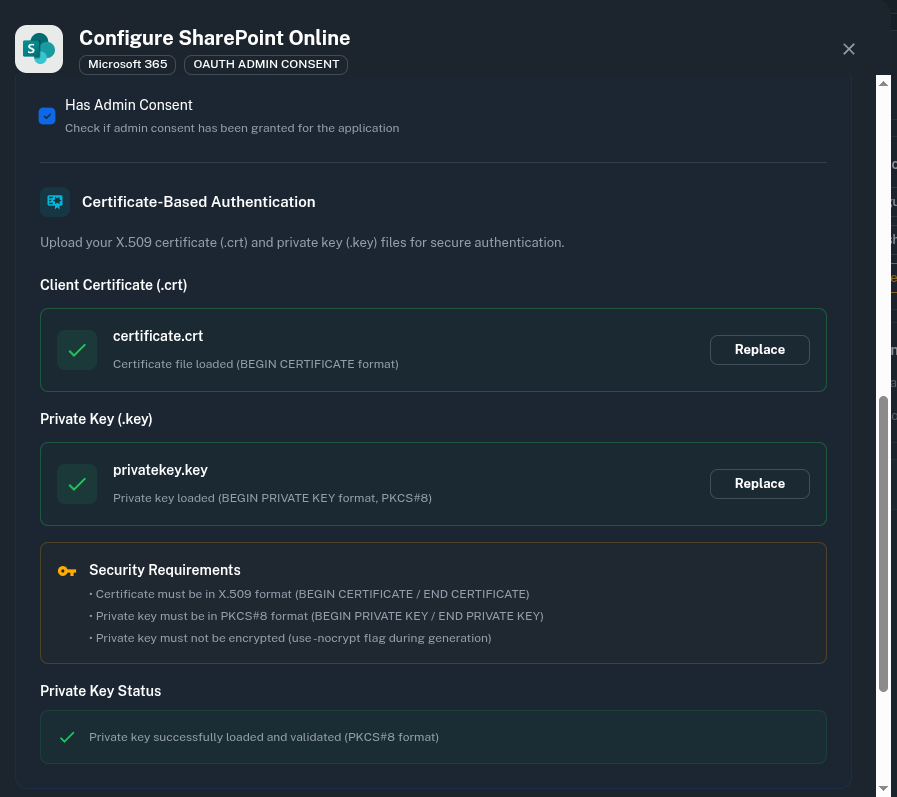
certificate.crt and privatekey.key exist. Open each file, and ensure the files conform to the following formats:- The certificate file must start with
BEGIN CERTIFICATEand end withEND CERTIFICATE - The private key should begin with
BEGIN PRIVATE KEYand end withEND PRIVATE KEY. It must not include RSA in the headers, nor be encrypted.
- Upload the
certificate.crtin PipesHub under Client Certificate - Upload the
privatekey.keyin PipesHub under Private Key
- Navigate back to Microsoft Entra ID > Manage > App registrations and click on the app you created earlier
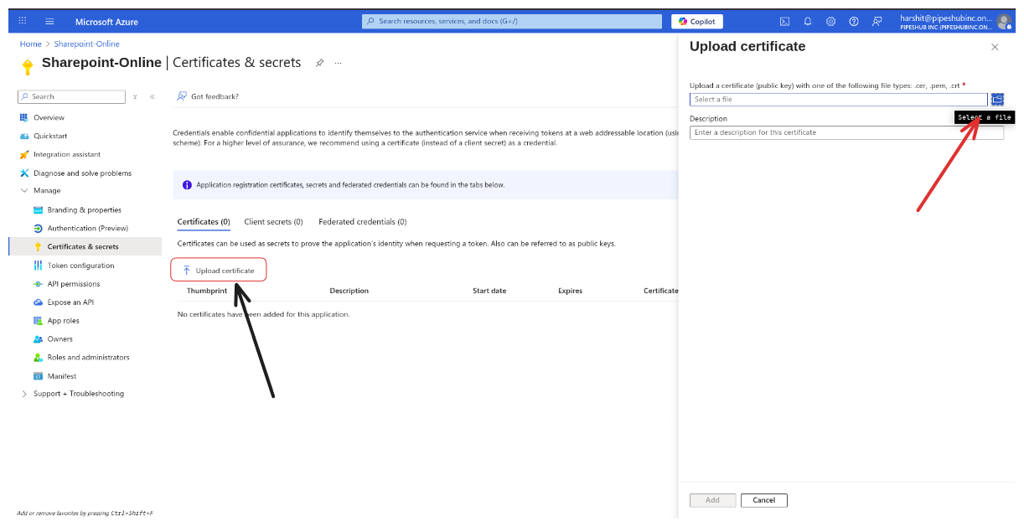
- Click Manage > Certificates & secrets
- Click the Certificates section and Upload certificate
- Upload the
certificate.crtfile that you generated - After uploading, the application must now list the new certificate